2.1 How Blockchain Works
- Block chain is a type of diary or spreadsheet containing information about transaction & each transaction is generate a hash.
- A hash is combination of string & numbers.
- Transaction are entered in order. Order is very important.
- Hash dependence not only transaction but also previous transaction hash.
- Every small changes in a transaction create new hash.
- The nodes check to make sure a transaction has not been changed by inspection the hash.
- If transaction approved by majority of nodes, then it written into a block.
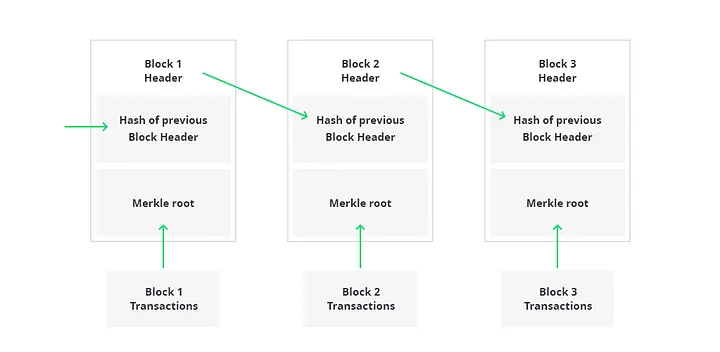
- Each block refer to the previous block & together they make the Blockchain.
- Blockchain update itself every 10 minutes
2.2.Structure of Blockchain
The structure of block chain technology is represented by a list of blocks with transaction in a particular order. These lists can be stored as a flat file (txt. format) or in the form of a simple database.
Block chain use two data structure:
- Pointers: variables that keep information about the location of another variable. Specifically, this is pointing to the position of another variable.
- Linked List: a sequence of blocks where each block has specific data and links to the following block with the help of a pointer
Types of Blockchain:
Public Blockchain Architecture:
- A public blockchain architecture means that the data and access to the system is available to anyone who is willing to participate (e.g. Bitcoin, Ethereum, and Litecoin blockchain systems are public).
- All records are visible in public & anyone could take part in the agreement process.
- It is open-source, no charge, distributed & decentralized public ledger so anyone can review anything on a public Blockchain.
- This architecture to be permission less block chain.
Private Blockchain Architecture:
- As opposed to public blockchain architecture, the private system is controlled only by users from a specific organization or authorized users who have an invitation for participation.
- It is controlled by single organization that determines who can read it, submit the transaction to it,& who can participate in the consensus process.
- permissioned block chain.This architecture to be
Consortium Blockchain Architecture:
- this architecture controlled by group of companies or representative individual.
- These pre-selected groups are coming together & make decision for the best benefit of the whole network
2.3.Block
Genesis Block:
- genesis block is the first block in any blockchain-based protocol. It is the basis on which additional blocks are added to form a chain of The blocks, hence the term blockchain
- This block is sometimes referred to Block 0. Every block in a blockchain stores a reference to the previous block. In the case of Genesis Block, there is no previous block for reference. it means that the Genesis Block has it's "previous hash" value set to 0. This means that no data was processed before the Genesis Block
- All other blocks will have sequential numbers starting by 1, and will have a "previous hash" set to the hash of the previous block.
- Every block must include three things:
- A hash pointer to the previous block
- Timestamp
- List of transactions
2.4.Hash
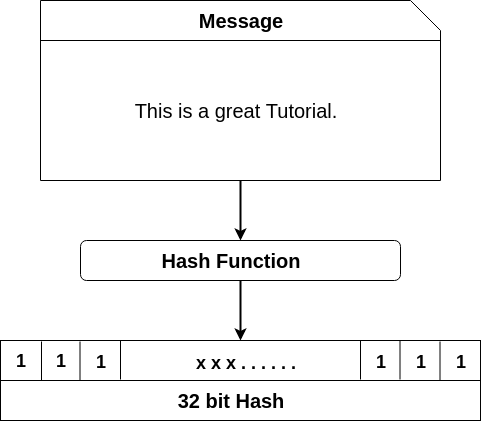
A hash function takes an input string (numbers, alphabets, media files) of any length and transforms it into a fixed length. The fixed bit length can vary (like 32-bit or 64-bit or 128-bit or 256-bit) depending on the hash function which is being used. The fixed-length output is called a hash.
We can understand it from the following diagram.
Following are the secure hash algorithm:
MD5
- Message-Digest Algorithm: This family comprises hash functions MD2, MD4, MD5, and MD6.
- MD5 is the most widely used cryptographic hash function.
- It is used to generate a 128-bit digest from a 512-bit string broken down into 16 words composed of 32 bits each.
- Ronald Rivest designed this algorithm in 1991 to use for digital signature verification.
- These are no longer considered cryptographically secure methods and should not be used for cryptographic authentication.
SHA256
- A Bitcoin's blockchain uses SHA-256 (Secure Hash Algorithm) hashing algorithm. In 2001, SHA-256 Hashing algorithm was developed by the National Security Agency (NSA) in the USA
- SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates.
- A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions.
- Hashing is similar to encryption, the only difference between hashing and encryption is that hashing is one-way, meaning once the data is hashed, the resulting hash digest cannot be cracked, unless a brute force attack is used.
- See the image below for the working of SHA algorithm. SHA works in such a way even if a single character of the message changed, then it will generate a different hash. For example, hashing of two similar, but different messages i.e., Heaven and heaven is different. However, there is only a difference of a capital and small letter.
- When learning about SHA forms, several different types of SHA are referenced. Examples of SHA names used are SHA-1, SHA-2, SHA-256, SHA-512, SHA-224, and SHA-384, but in actuality there are only two types: SHA-1 and SHA-2. The other larger numbers, like SHA-256, are just versions of SHA-2 that note the bit lengths of the SHA-2. SHA-1 was the original secure hashing algorithm, returning a 160-bit hash digest after hashing.
- SHA-2 can produce a variety of bit-lengths, from 256 to 512 bit, allowing it to assign completely unique values to every hash digest created.
2.5. Blockchain
| BLockChain | Database | |
|---|---|---|
| Definition | It is peer-to-peer decentralized distributed technology. It is a secure series or chain of the timestamp record stored in database | Database are centralized ledger which store data in a structure way & is Managed by an administrator |
| Authority | Blockchain is decentralized and has no centralized approach | Database are controlled by the administrator and centralized in nature. |
| Architecture | It uses a distributed ledger network architecture (P2P) | It uses client server architecture |
| Data Handling | Blockchain utilizes read & write operation | Database supports create, update, delete etc. |
| Transparency | Public Blockchain offers transparency | Database is not transparent. Only administration decides which data public can access |
| Cost | Blockchain are comparatively harder to implement & maintain | Database being an old technology is easy to implement and maintain |
| Performance | Blockchain is down by verification and consensus methods. | Databases are extremely fast and offer great scalability |
| Best use Cases | Transfer value storage value Voting System Trusted data verification | Storing Data Relational Database |
2.6. Distributed
Operation of distributed Ledgers:
the ownership and transfer of digital asset is commonly recorded on a blockchain or the other distributed ledger. typically distributed ledger operate through the use of public and private key the distributed ledger show which public key owns each digital asset.
the affect the transfer of a Digital asset the Transferor needs to enter the private key that corresponds to the public key that the ledger show as the owner of the digital asset. private keys are created in mathematical relation to their public key pair and are unmodifiable.
Participants in the distributed ledger validate transactions by confirming that the transfer has been authorized by the private key associated with the relevant public key.
Through the possession and use of a private key validate to digital asset transfers every assest recorded on a specified distribute ledger may be transferred between different public keys. Without public key private key match however no assets held in connection.
As a result digital asset investors must be able to effictivley retain and protect such private key information and thus control over all attach digital asset to protect their investments
Goals of Distributed Ledgers:
2.7. Lifecycle of Blockchain
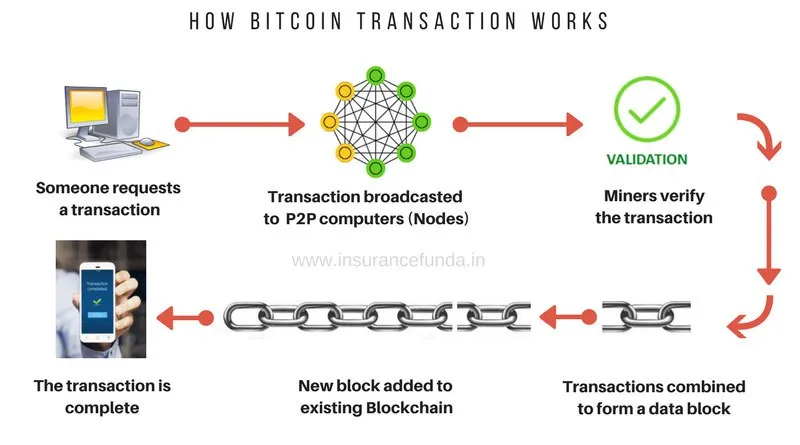
The steps in lifecycle of Blockchain are:
- Someone requests a transaction via something called a wallet
- The transaction is send to all participation computers in the specific Blockchain network
- Every computer in the network checks the transaction against some validation rules that are set by the creators of the of the specific Blockchain network
- Validated transactions are stored into a block and are sealed with lock
- This block becomes part of the Blockchain when other computers in the networks validate if the lock on the block is correct
- Now the transaction is part of the blockchain and connect be altered in any way.
2.8. Smart Contract
- Smart contracts are simply programs stored on a blockchain that run when predetermined conditions are met. At the most basic level they are programs that run as they have been set up to run by the people who developed them
- They can be used to formalize simple agreements between two parties the bylaws of an organization or create tokens
- A small contract is a self-enforcing piece of software that is managed by p2p network of computers. Smart contracts are used right management tools that provide a coordination and enforcement between network participants
- Then benefits of smart contracts are most apparent in business collaborations in which they are typically used to enforce some type of agreement so that all.
- Participants can certain of the outcome without an intermediary involvement.
- Smart contracts work by following simple "if/when...then.." statements that are written into code on a blockchain. A network of computers executes the actions when predetermined conditions have been met and verified.
- Benefits of smart contracts:
- Speed and accuracy
- Trust
- Security
- Savings
Aspects of smart Contracts:
2.12 Practical Byzantine
- Practical Byzantine Fault Tolerance is a consensus algorithm introduced in the late 90s by Barbara Liskov and Miguel Castro.
- pBFT was designed to work efficiently in asynchronous(no upper bound on when the response to the request will be received) systems.
- It is optimized for low overhead time.
- Its goal was to solve many problems associated with already available Byzantine Fault Tolerance solutions.
- Application areas include distributed computing and blockchain.
- A client sends a request to the leader node to invoke a service operation.
- The leading node broadcasts the request to the backup nodes.
- The nodes execute the request, then send a reply to the client.
- The client awaits f+1 replies from different nodes with the same result, where f represents the maximum number of potentially faulty nodes.
pBFT consensus rounds are called views and are broken into 4 phases:
2.13 Fault Tolerance
- The ability of maintaining functionality when portions of a system break down is referred to as graceful degradation. Byzantine fault tolerance can be achieved if the correctly working nodes in the network reach an agreement on their values.
- A practical byzantine fault tolerant system can function on the condition that the maximum number of malicious nodes must not be greater than or equal to one-third of all the nodes in the system. As the number of nodes increase the system becomes more secure.
Advantages of pbft:
- Energy efficiency : pBFT can achieve distributed consensus without carrying out complex mathematical computations(like in PoW). Zilliqa employs pBFT in combination with PoW-like complex computations round for every 100th block.
- Transaction finality : The transactions do not require multiple confirmations(like in case of PoW mechanism in Bitcoin where every node individually verifies all the transactions before adding the new block to the blockchain; confirmations can take between 10-60 minutes depending upon how many entities confirm the new block) after they have been finalized and agreed upon.
- Low reward variance : Every node in the network takes part in responding to the request by the client and hence every node can be incentivized leading to low variance in rewarding the nodes that help in decision making.
Limitations of pBFT:
- Sybil attacks : The pBFT mechanisms are susceptible to Sybil attacks, where one entity(party) controls many identities. As the number of nodes in the network increase, sybil attacks become increasingly difficult to carry out. But as pBFT mechanisms have scalability issues too, the pBFT mechanism is used in combination with other mechanism(s).
- Scaling : pBFT does not scale well because of its communication(with all the other nodes at every step) overhead. As the number of nodes in the network increase (increases as O(n^k), where n is the messages and k is the number of nodes), so does the time taken to respond to the request.
The pBFT consensus model works efficiently only when the number of nodes in the distributed network is small due to the high communication overhead that increases exponentially with every extra node in the network.
2.14 Actors of Blockchain
An entity that can participate in an action or in a blockchain network is known as an actor, which is an abbreviation of blockchain actor. Each actor has defined and key role to play in the development, operation and maintenance of the Blockchain network.
2.15 Blockchain developer
The developer of applications and smart contracts that interact with the blockchain and are used by the blockchain users. The blockchain developer is the one who is going to take what has been an architect and then develop the actual code that will run on the blockchain network itself.
2.16 Blockchain operator
User have special permission and authority to define, create, manage and monitor the Blockchain network are known as Blockchain operator. Each business on a Blockchain network has a Blockchain network operator.
2.17 Blockchain regulator
The overall authority is a business network. Specifically, regulators are required to read the ledger’s content broadly. The Blockchain regulator is an optional one, they might have only, read-only access onto the network where they see the transactions being performed are legitimate or not, following policies or not, etc.
2.18 Blockchain user
The business user, operating in a business network. User experiences the application of that blockchain solution. They are not aware of blockchain. Blockchain user is the one who is going to perform the business transactions on the blockchain, so, these users could belong to multiple organizations that are participating in that blockchain.
2.19 Membership service provider
It is a modular component that is used to manage identities on the blockchain network.
This provider is used to authenticate clients who want to join the blockchain network. Blockchain participants need a way to prove their identity to the rest of the network in order to transact on the network.
Certificate authorities issue identities by generating a public and private key which forms a key- pair that can be used to prove identity. Because private key never share publicly.
The MSP is the mechanism that allow that identify to be trusted and recognized by the rest of the network without ever revealing the members private key
Domains of membership service provider:
1) Locally on an Actor's node(Local MSP)
Local MSPs are defined for clients and for nodes.
In Channel Configuration (Channel MSP)
Channel MSPs define administrative and participatory rights at the channel level.

No comments:
Post a Comment